针对Typecho搜索框的两种形式Get请求的CSRF防御功能:index.php:
$referer = $_SERVER["HTTP_REFERER"];
$url = 'http://'.$_SERVER['HTTP_HOST'].$_SERVER['REQUEST_URI'];
if ((preg_match("/blog.diannao120.top\/\?s\=/i", "$url") || preg_match("/blog.diannao120.top\/index.php\/search/i", "$url")) && !preg_match("/blog.diannao120.top/i", "$referer")) {
http_response_code(403);
exit('<h2>CSRF Request is Forbidden !</h2>');
}这样实际上解决问题了,会对不适当请求返回403状态码同时拒绝服务,但是漏洞扫描还会报漏洞: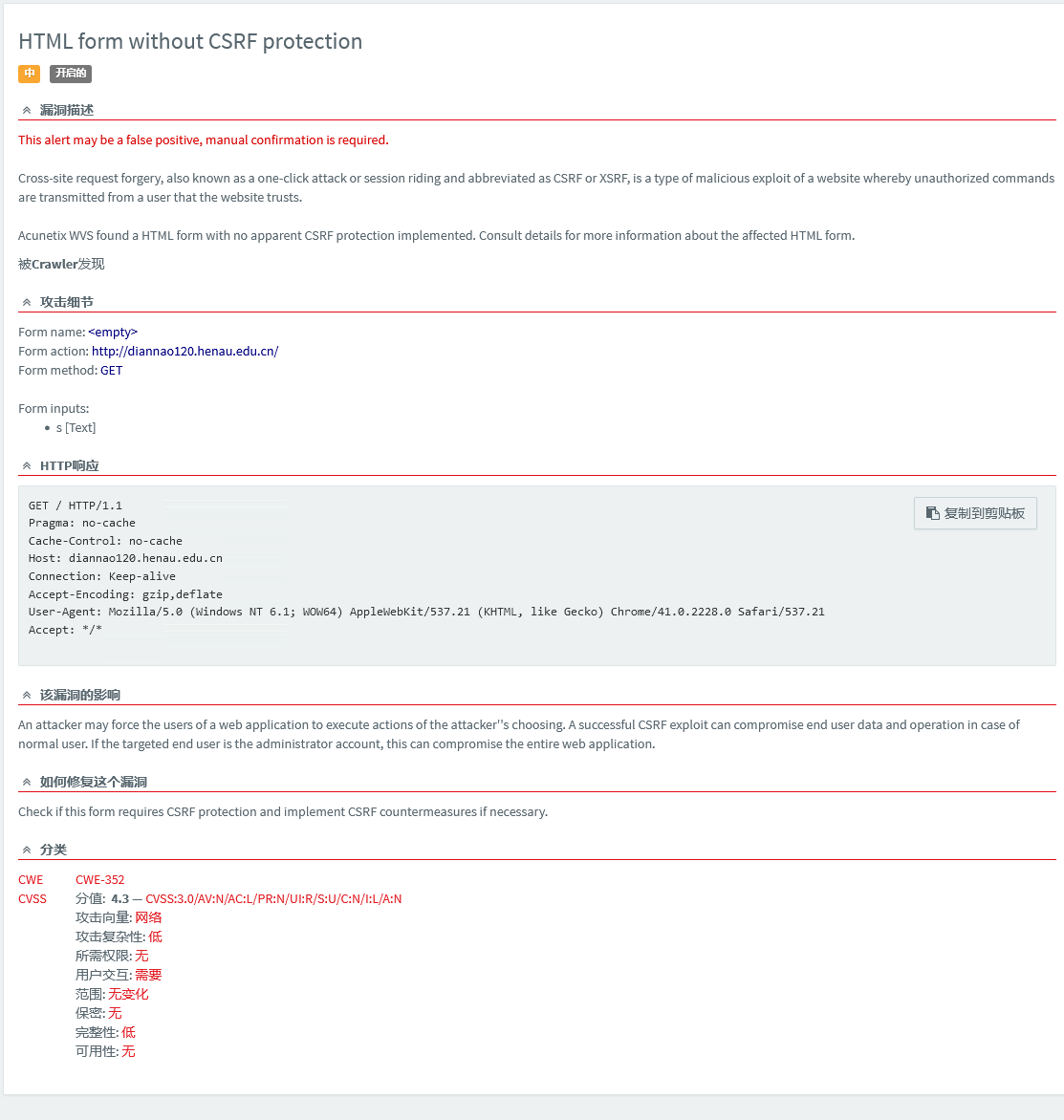
10.19凌晨更新:
偶然发现河南农业大学招生办公室网站搜索框有一个隐藏的input,不抱希望的把它拿来一试,竟然过了!Nice!
<input type="hidden" name="kwtype" value="0">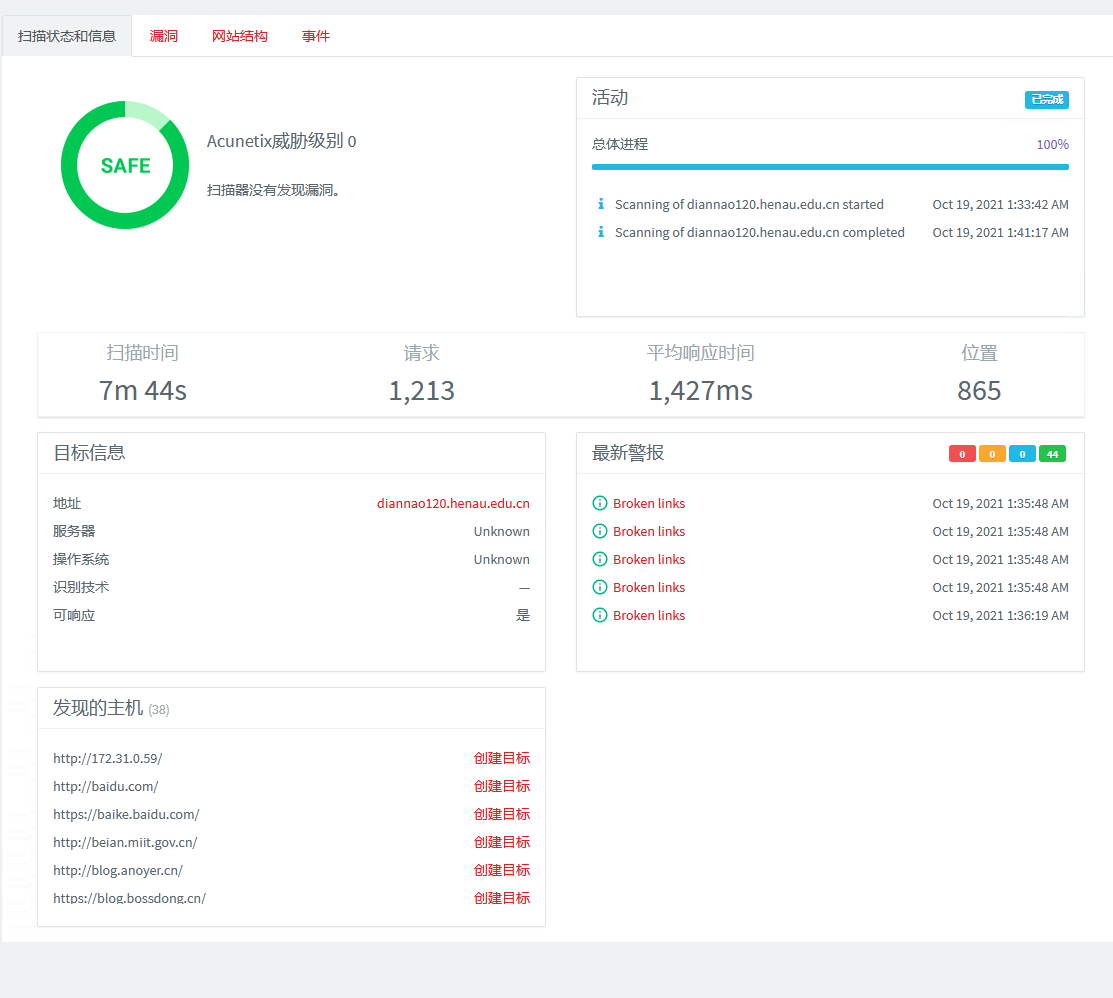
参考资料:
https://blog.csdn.net/zhongliang415/article/details/108300607
https://blog.csdn.net/tterminator/article/details/70186033
https://www.lanka.cn/typecho-5_3736.html
https://www.cnblogs.com/shikyoh/p/4959678.html
https://www.runoob.com/php/php-preg_match.html
https://www.cnblogs.com/xinaixia/p/5852379.html
https://blog.csdn.net/senlin1202/article/details/50800146
https://www.cnblogs.com/ronghua/p/11347090.html
https://blog.csdn.net/weixin_33669968/article/details/88889748
https://blog.csdn.net/xiaohuangren_123/article/details/115208779
版权属于:soarli
本文链接:https://blog.soarli.top/archives/561.html
转载时须注明出处及本声明。